AIM
4/3/14
5−6−4
National Security and Interception Procedures
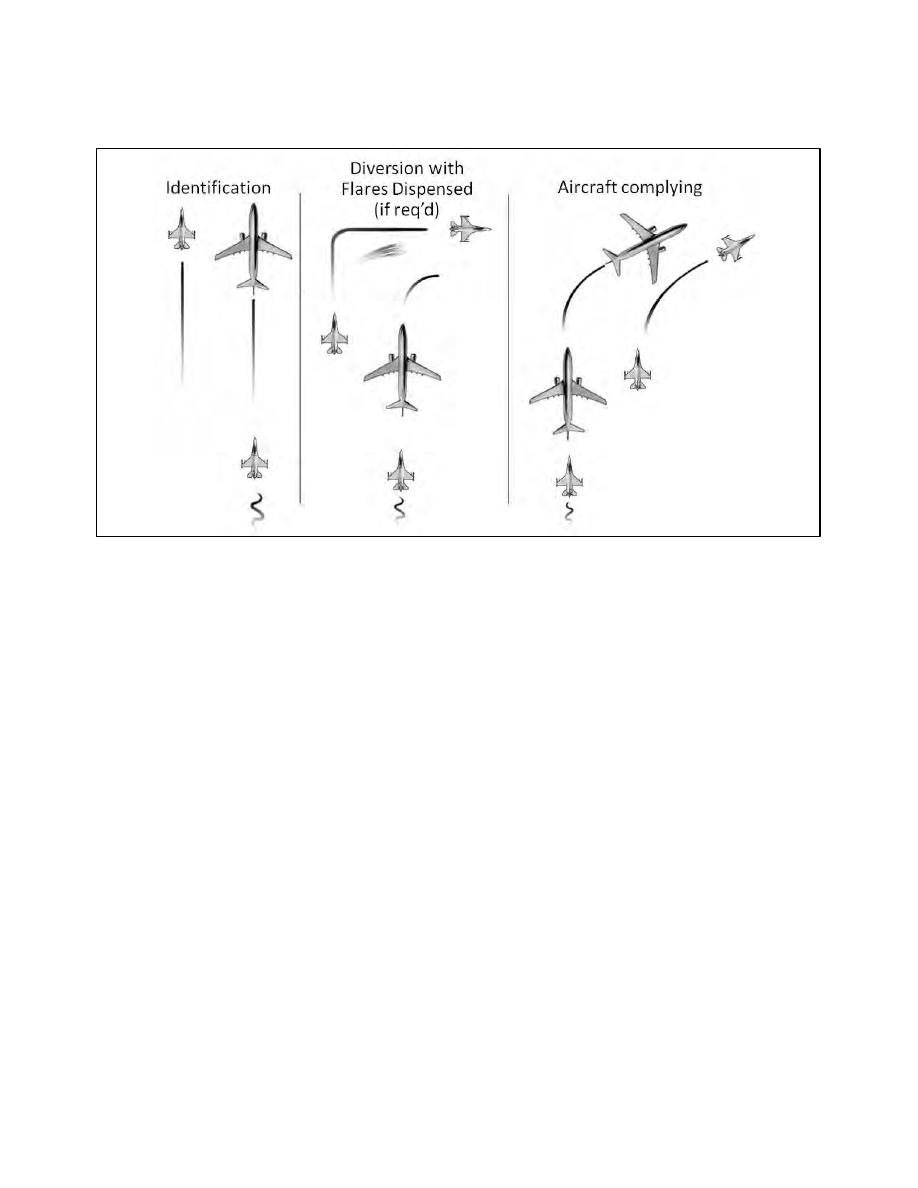
FIG 5
−6−1
Intercept Procedures
| Previous Page | Page 396 | Next Page |

AIM
4/3/14
5−6−4
National Security and Interception Procedures
FIG 5
−6−1
Intercept Procedures
| Previous Page | Page 396 | Next Page |